Test Your Internet speed
our hacker news bulletin page
)-(
News may 09

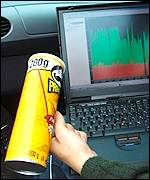
Empty Pringles crisps containers could be helping hackers find wireless connections that are open to attack.
Security company i-sec have demonstrated that a directional antenna made from a Pringles can significantly improves the chances of finding the wireless computer networks being used in London's financial district.
A survey carried out by i-sec using the homemade aerial found that over 60% of networks were doing nothing to protect there security.
The security firm said all the companies at risk could easily stop anyone that wanted to find their network by making a few simple changes to there hardware used to build the wireless networks.
These networks are rapidly becoming popular because they`r cheap, easy to set up & replace the unsightly cables that many companies have used to link PCs together into networks.
But the convenience of using radio waves to transfer data between machines isnt without risks.
Many curious hackers have started carrying out war-driving expeditions.
US security expert Peter Shipley invented the practice. It involves driving around an area using a laptop fitted with a wireless network card to find and map out the networks.
Wireless, or WiFi, networks have an encryption system built in, but it is not turned on when the basic hardware of the network is set up.
"Many companies are going out & buying a wireless access point to see what it can do," said Mr Davies. "The problem is that they have opened a great big back door into their network."
i-sec had boosted the chance of finding networks by converting an empty can of Pringles into a directional, or Yagi, antenna. Plans for making such an antenna first appeared on the net last year.
Properly made, such an antenna can boost signal strengths by up to 15 decibels, vastly aiding the discovery of wireless networks.
In one 30-minute journey using the Pringles antenna, i-sec managed to find nearly 60 wireless connections.
"People have made these antennae from Pringles tubes, coffee cans & satellite dishes," said Mr Davies.
Mr Davies said that a few easy steps like changing your default names, moving your wireless access points to the centre of the building & switching off the networks' broadcast functions could significantly improve security .

Researchers from the Computer Security Group of the University of California at Santa Barbara have taken control of the Torpig botnet for ten days. Their report reveals that the Trojan stole 8,310 accounts from 410 different financial institutions, as well as the details of 1,660 credit cards during the 10 day period alone.
Torpig, also known as Sinowal, is a 3 year-old banking trojan, which ranks pretty high amongst the most resilient and complex pieces of malware. The Trojan is being distributed through Mebroot, a rootkit that installs itself at the low level of a computer, inside the Master Boot Record , making it very resilient to av detection.
Another state of the art technique employed by Torpig is the domain flux, where a list of domain names is periodically generated by each infection according to an algorithm, which are then queried in order to locate a command and control server. The researchers hijacked the botnet by registering some of the domains in advance, before its owners succeeded in regaining control some ten days later.
While the driving force between the Torpig operation is the illegal monetary gain, the trojan does not only steal financial information, which is clearly the most valuable of all. The malware is able to log & sort user input into more than 29 popular applications, including the top 3 browsers, IE, Firefox & Opera, e-mail clients like Outlook, Thunderbird and Eudora, or instant messengers like ICQ or Skype. Login credentials, accounts and passwords are targeted.
Torpig instruments local phishing attacks, by injecting rogue forms into the legit pages loaded into the browsers. These forms ask users for their sensitive financial details and are hard to identify, because they can be inserted at the browser level at any point during the user session, even if the connection is established over SSL.
The researchers collected an impressive 70GB of data during the 10 days of hijacking & estimated that 182,800 bots connected to their C&C server. This number was determined after special methodology was used and not by counting unique IP addresses. In fact, a total number of 1,247,642 unique IPs were observed, forcing the researchers to conclude that, "Taking this value as the botnet size would overestimate the actual size by an order of magnitude."
Another interesting conclusion is the high possibility that the botnet, or, parts of it, are being lent to third-party criminals. This is suggested by unique and never-changing build names appended to all types of communications and the collected information. "The most convincing explanation of the build type is that it denotes different 'customers' of the Torpig botnet, who, presumably, get access to their data in exchange for a fee," the researchers note.
Even though much of the 70GB of data were login credentials for e-mail accounts- Gmail at the top, social networking services -Facebook at the top, & other non-financial related services, the leak of sensitive personal & banking information is still significant. The researchers counted compromised accounts from PayPal (1,770), Poste Italiane (765), Capital One (314), E*Trade (304), and Chase (217).
This seems to be partially consistent with the distribution of Torpig-infected machines across the globe: U.S (54,627), Italy (46,508), Germany (24,413), to name the top three countries, which are also the only ones over the 7,000-bot mark. The botnet also has a great potential to launch Denial of Service attacks, aggregating a bandwidth of over 17 Gbps from DSL/Cable connections
.
An interesting analysis regarding the security habits of the affected users was also performed. The researchers subjected the 173,686 collected passwords to the popular John the Ripper password-cracking tool. In under 75 minutes, the program was able to recover 40% through dictionary attacks. 30,000 more were cracked in the next 24 hours through a brute force approach.
The analysis found that almost 28% of its victims reused their credentials for accessing 368,501 web sites, the report also notes. This led the researchers to conclude that, "The victims of botnets are users with poorly maintained machines that choose easily guessable passwords to protect access to sensitive sites. This is evidence that the malware problem is fundamentally a cultural problem."
The success of Torpig inspired & still continues to inspire other malware authors, who borrowed & improved the techniques employed by this application. Due to its success, Torpig's own creators are putting a lot of effort into its maintenance. In November 2008 a report regarding the trojan's activity, researchers from RSA Security noted that, "Almost three years is a long time for just one online gang to maintain the lifecycle and operations in order to effectively utilize just one Trojan."
We have just reported that malware experts from security vendor Prevx have identified and analyzed a completely revamped version of the Mebroot rootkit, which displays highly complex detection-evading mechanisms. "Even if the first MBR rootkit variant is still undetected by some antivirus vendors, its creators decided to develop a new version of it, virtually able to bypass almost all security products, even the ones able to detect the first version," one of Prevx's researchers, Marco Giuliani, warned.
:- )
page 2 of hacker news
ii- Hackers breach pentagon security
iii-Hacker indicted on cisco attacks
Try the pr search tool to see how your site is ranked
If youve an interest in learning about hacking but dont know where to start
checkout the beginners section for a full list of what you need to know & how
to go about it- & once youve progressed a touch try the links to some of the hacking resources & forums :-0



0 comments:
Post a Comment